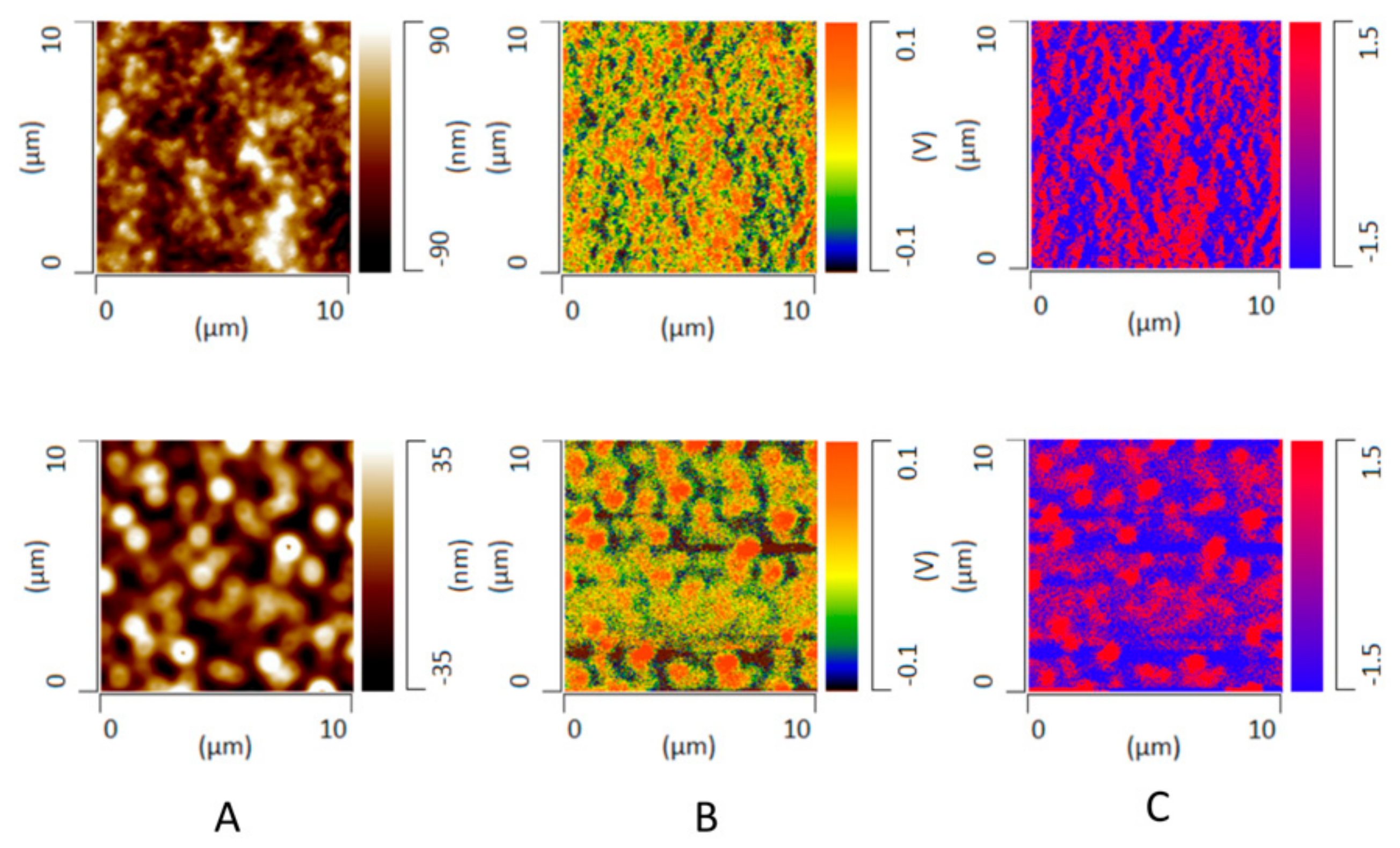
Pharmaceutics | Free Full-Text | Exploring the Role of Surfactants in Enhancing Drug Release from Amorphous Solid Dispersions at Higher Drug Loadings | HTML
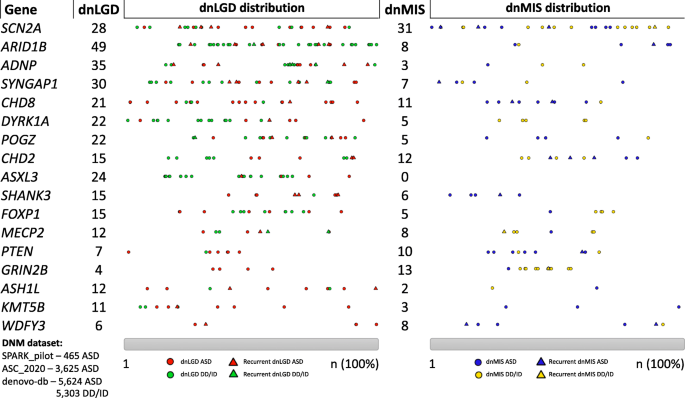
Reflections on the genetics-first approach to advancements in molecular genetic and neurobiological research on neurodevelopmental disorders | Journal of Neurodevelopmental Disorders | Full Text

ASSR power analysis. Top panels (a, b): ASSR beamformer localization.... | Download Scientific Diagram
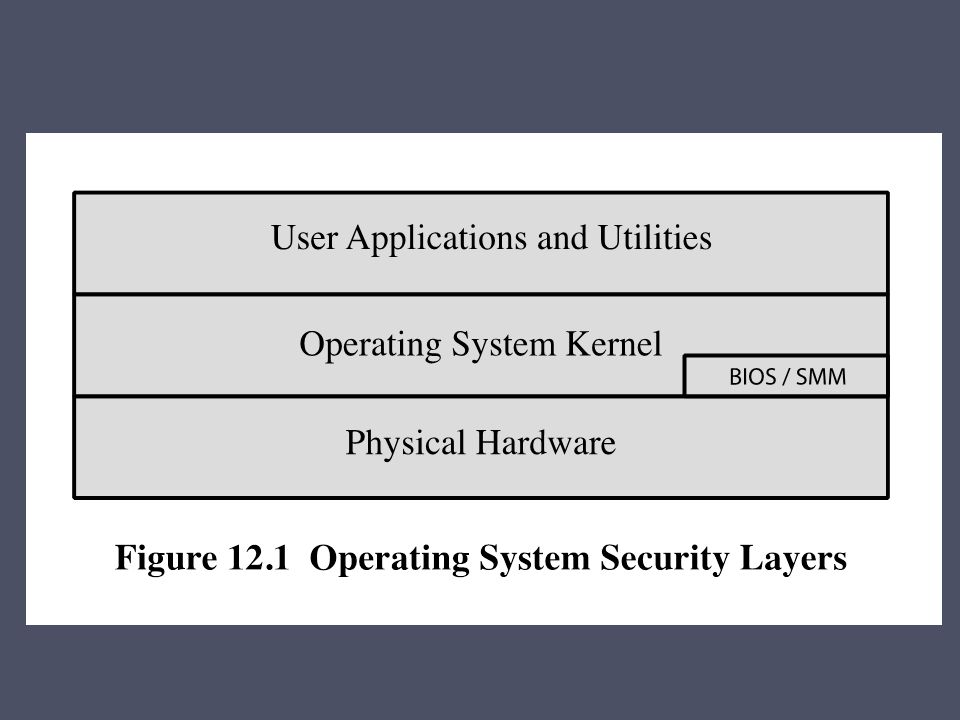
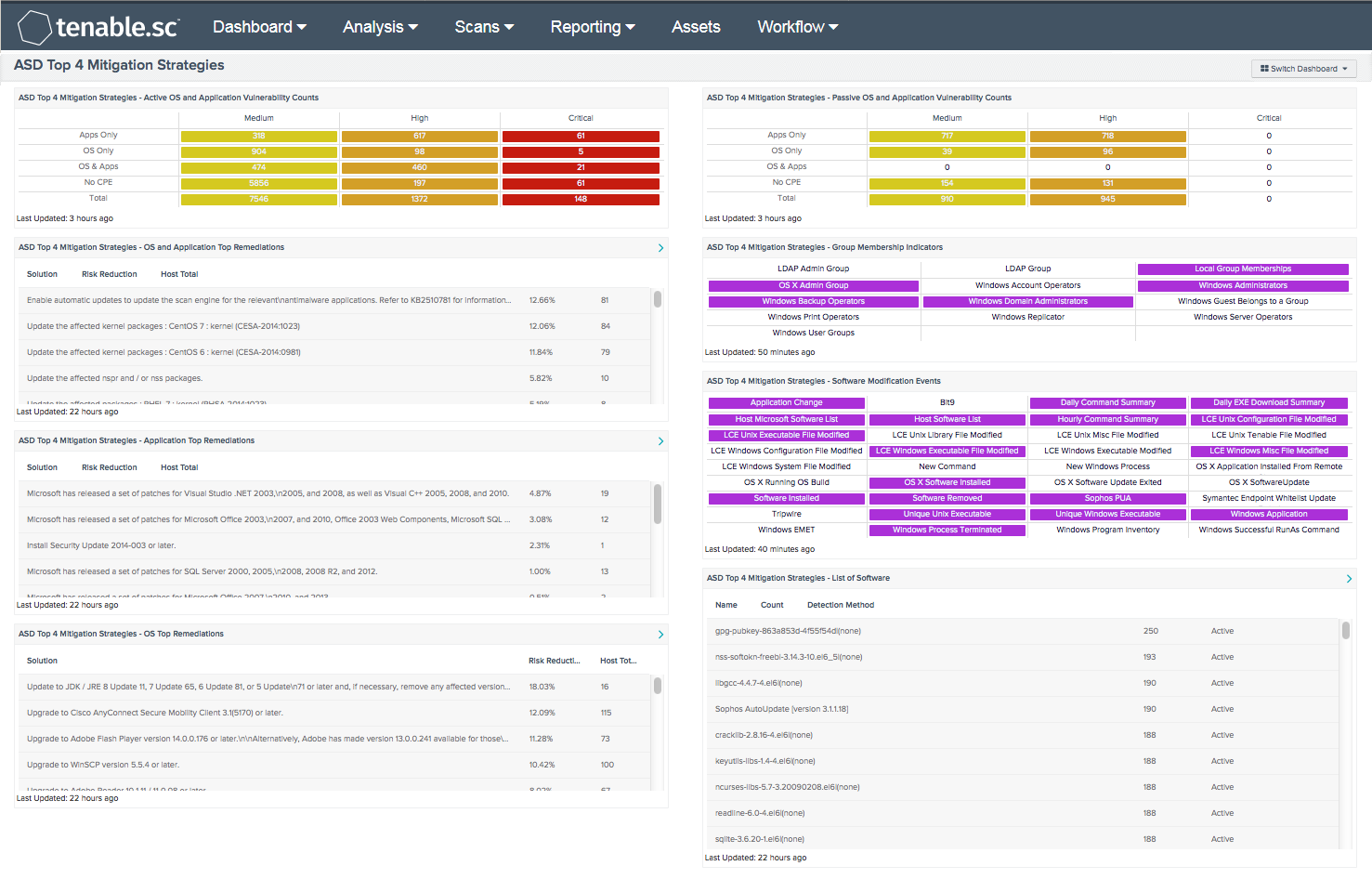
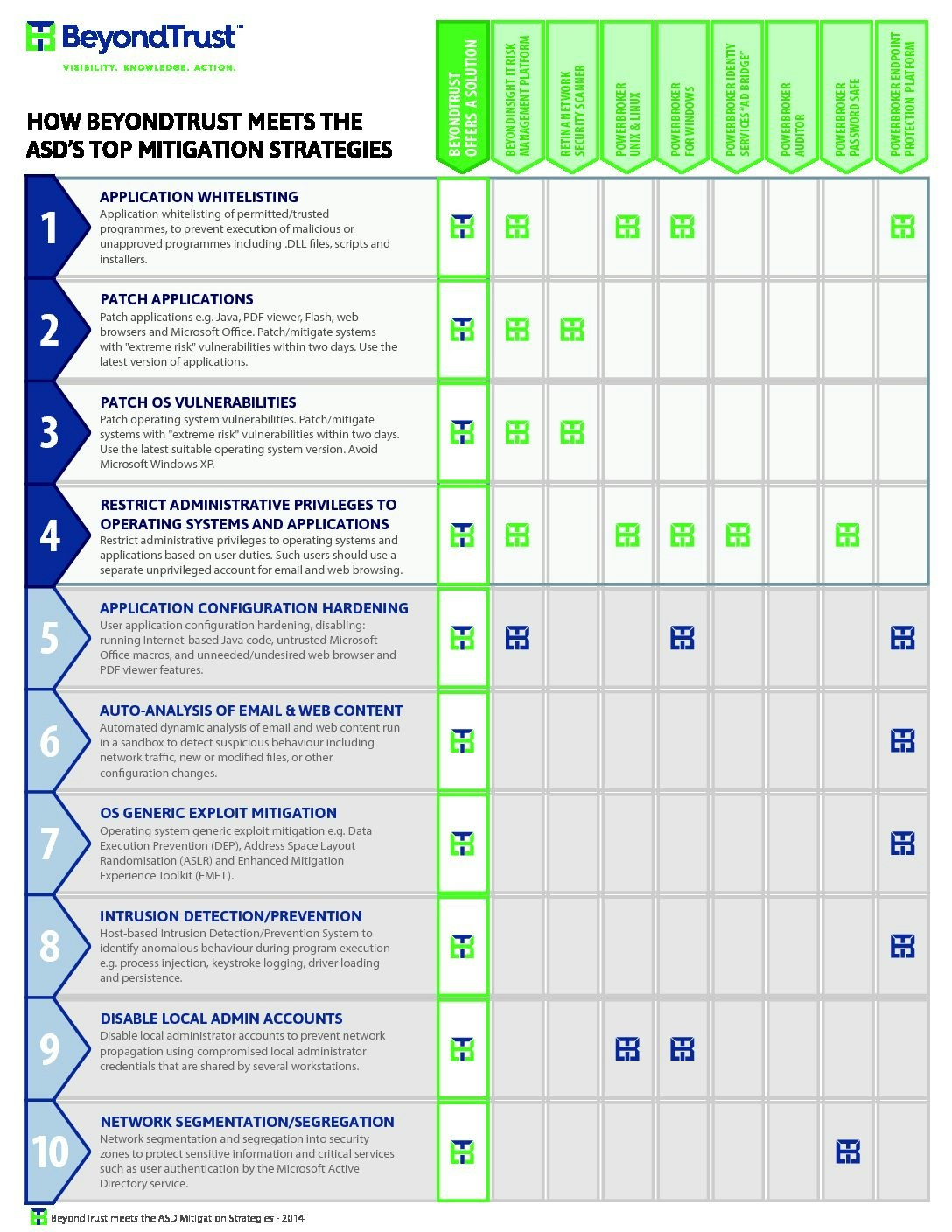
Chapter 12 Operating System Security Strategies The 2010 Australian Signals Directorate (ASD) lists the “Top 35 Mitigation Strategies” Over 85% of. - ppt download
34 LONG condition between TD and ASD. Top figure illustrates the t/f... | Download Scientific Diagram

Chapter 12 Operating System Security Strategies The 2010 Australian Signals Directorate (ASD) lists the “Top 35 Mitigation Strategies” Over 85% of. - ppt download
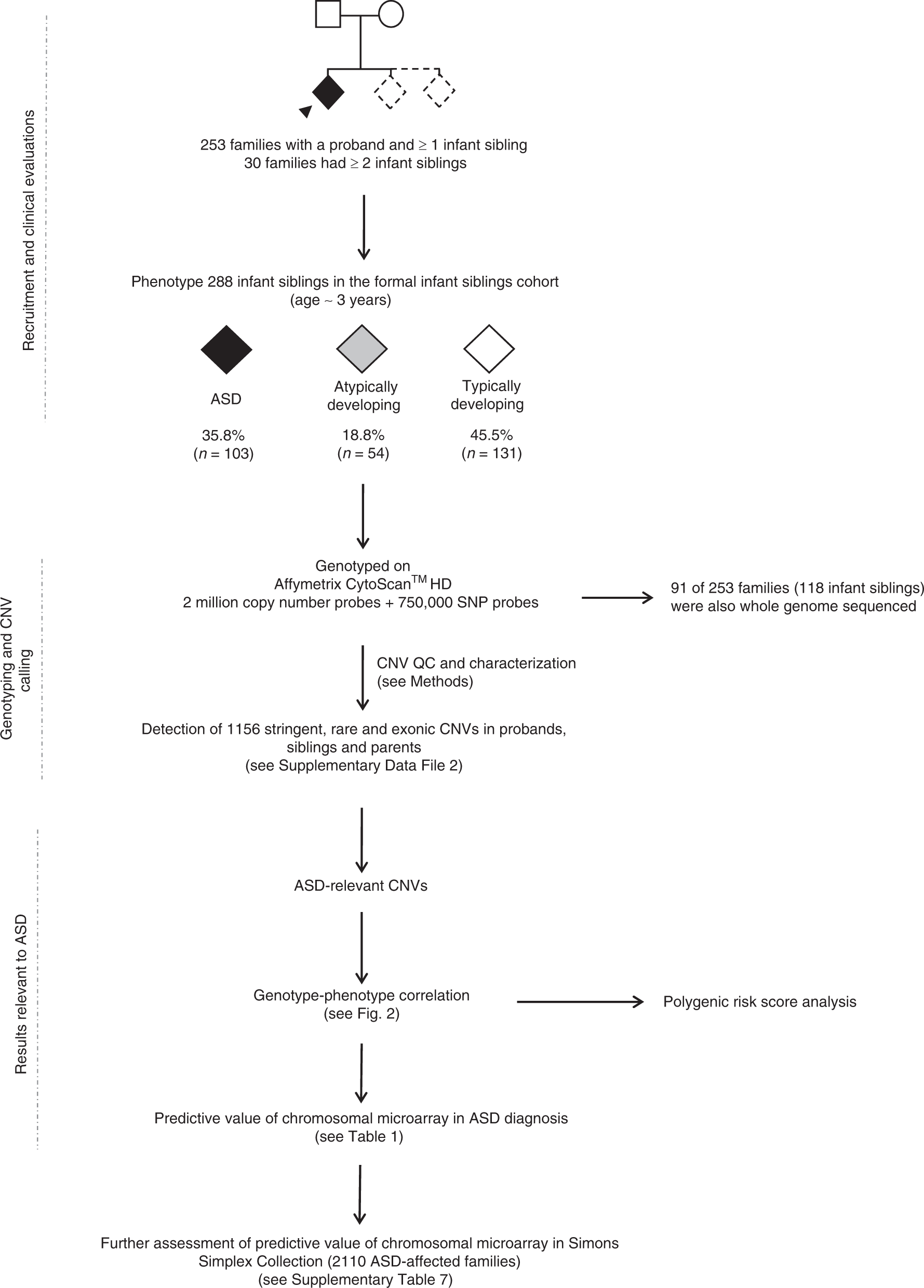
Predictive impact of rare genomic copy number variations in siblings of individuals with autism spectrum disorders | Nature Communications
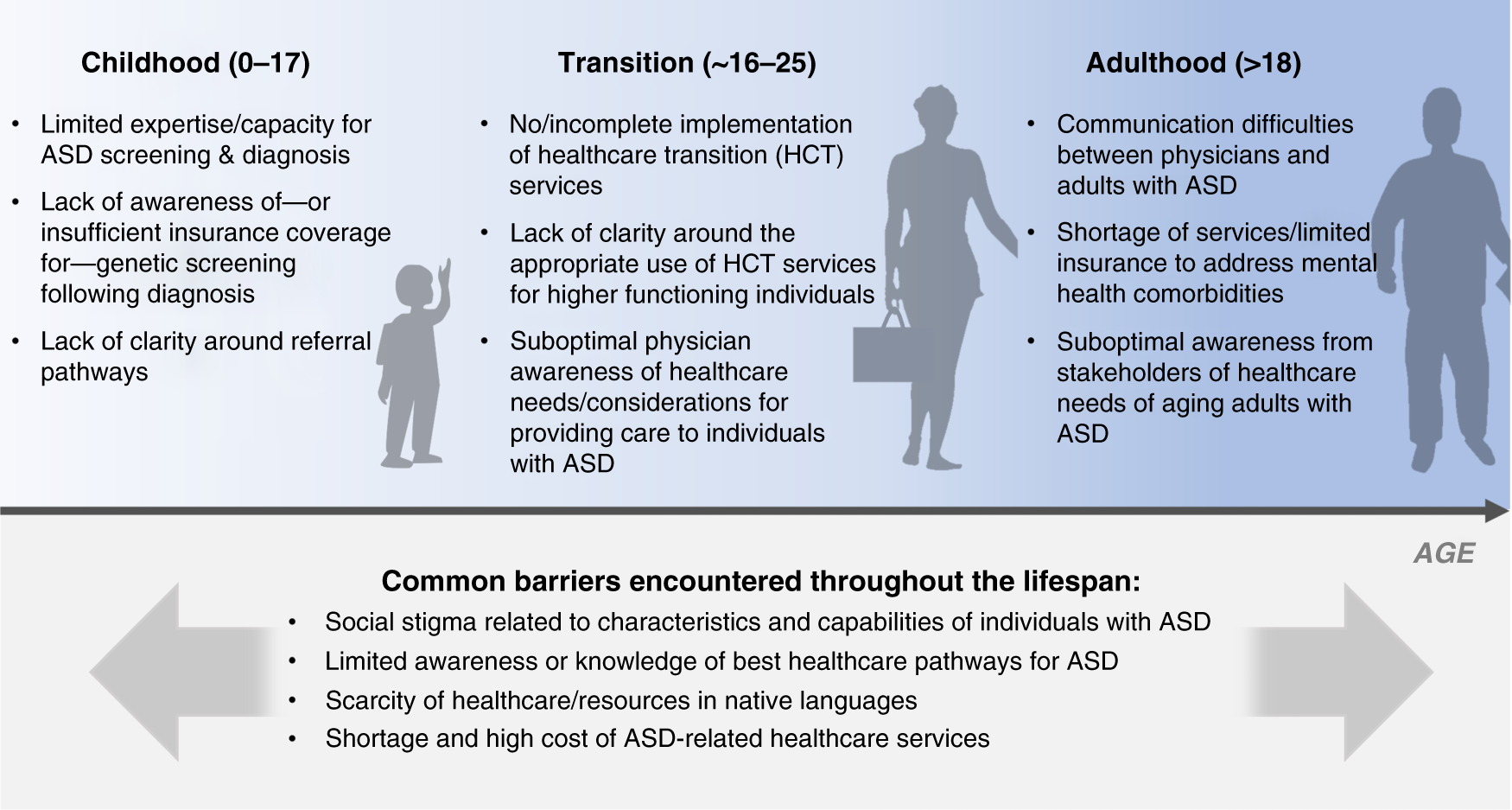
Tackling healthcare access barriers for individuals with autism from diagnosis to adulthood | Pediatric Research

Situational Crime Prevention and the Mitigation of Cloud Computing Threats Chaz Vidal Supervisor: Raymond Choo. - ppt video online download

![CERT Australia Update, by Scott Brown [APNIC 38 / Network Abuse BoF] CERT Australia Update, by Scott Brown [APNIC 38 / Network Abuse BoF]](https://image.slidesharecdn.com/certaustralia-engagement-apnic382014networkabusebof1410842858-140916001728-phpapp01/95/cert-australia-update-by-scott-brown-apnic-38-network-abuse-bof-20-638.jpg?cb=1410993094)




![Protecting Your Data Wherever it Goes [Infographic] - Verizon Small Business Essentials Resources Protecting Your Data Wherever it Goes [Infographic] - Verizon Small Business Essentials Resources](https://s2.yimg.com/lm/ysbp/img/8HSAw3_UtdkoHw_IJ6HcLIwymps_l5jp0fq3kbQsTqTeLdr2tvPbM5SEhADGE2wj.jpg)